Articles

Samsung TV Remote Troubleshooting
Samsung TV remotes are essential for a smooth viewing experience. When they stop working, it can be frustrating. The most ...
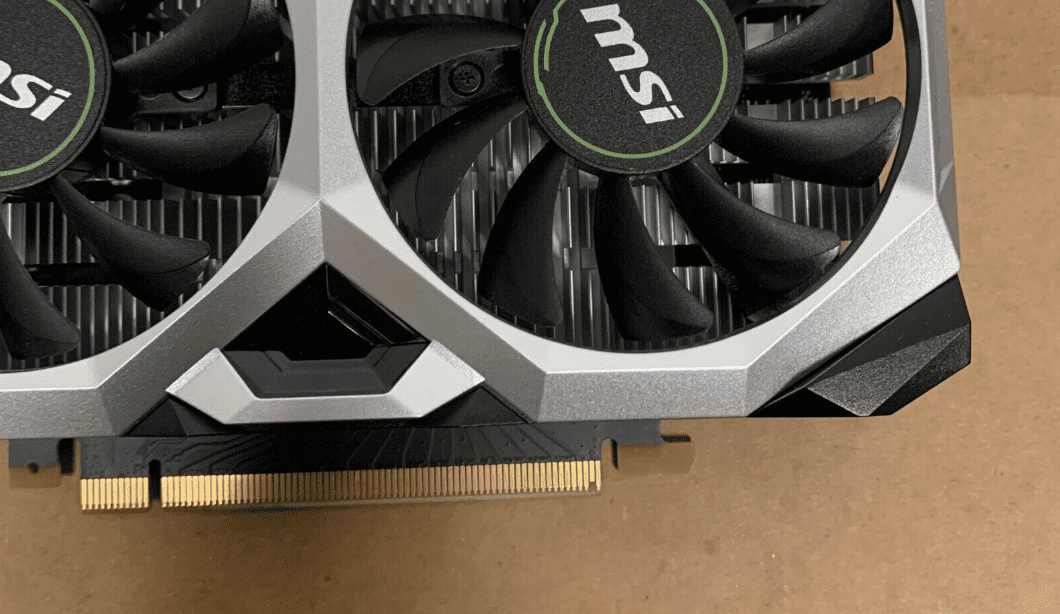
My Graphics Card Has A Short Or Missing Pin – What Do I do?
A missing or broken pin on your graphics card may seem like a disaster, but it’s not necessarily the end ...

Is It OK to Leave a Gaming Laptop On Overnight?
If you’re wondering whether it’s safe to leave your gaming laptop running overnight, the answer is generally yes, as long ...

GeForce RTX 5060: Nvidia’s Upcoming Gaming Powerhouse
The Nvidia GeForce RTX 5060 is set to be a new graphics card for gamers and PC enthusiasts. It’s expected ...

How to Update AMD Drivers
Keeping your AMD graphics drivers up-to-date is vital for optimal PC performance. Outdated drivers can lead to glitches, crashes, and ...

Best AM5 Motherboards: Top Picks for 2025
AMD’s new AM5 socket brings exciting changes for PC builders. It supports the latest Ryzen 7000 and 9000 series processors, ...

Top Choices For Point-to-Point Wireless Bridges
Wireless bridges are an important technology that enables the connection of networks across different physical locations. They provide a cost-effective ...
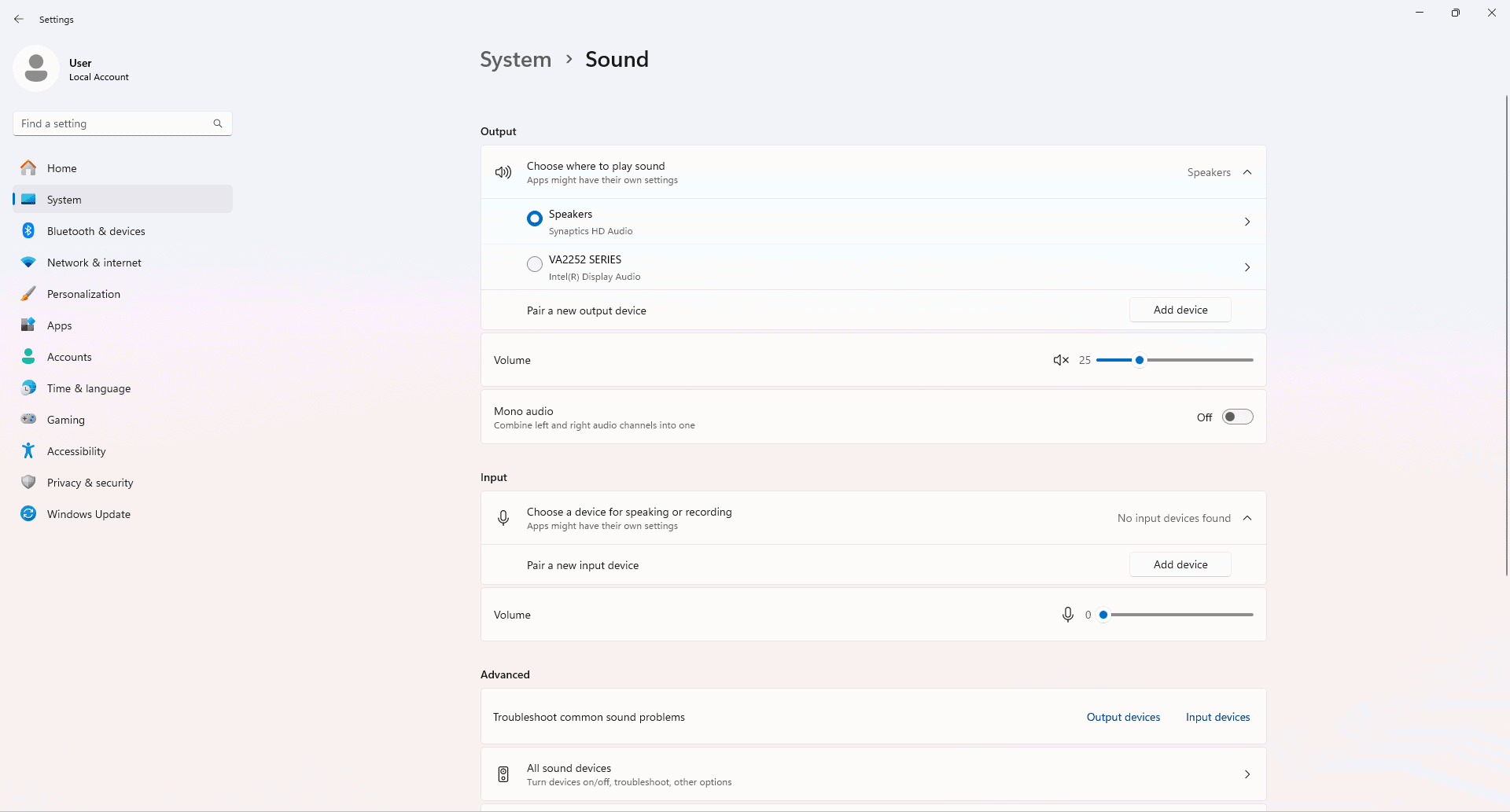
PC Won’t Play Sound: Troubleshooting
Having trouble with your computer’s sound? Don’t worry, many issues can be fixed with these simple steps. First, make sure ...

How to Fix “Your PC Ran into a Problem and Needs to Restart” Error
If you get the “Your PC ran into a problem and needs to restart” error message you could be wondering ...
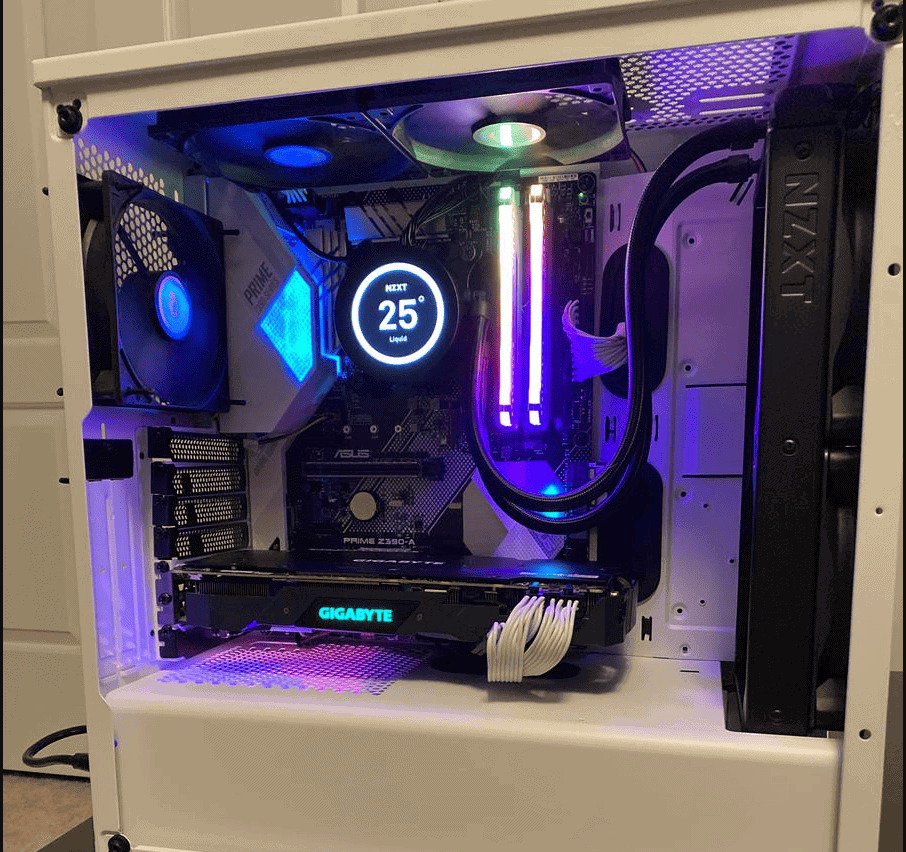
How To Upgrade Your Gaming PC (2025 Edition)
Ready to elevate your gaming experience? Upgrading your PC can be straightforward. Whether you want smoother gameplay, faster loading times, ...






